Security Considerations of Confidential Computing in Open Infrastructure
Author: Nicolae Paladi, CEO and Co-founder of CanaryBit
Confidential computing enables isolation of sensitive data in a secure domain during processing. It protects data in use by running the computation in a Trusted Execution Environment created using a combination of firmware and hardware features.
While the approach started with process-based isolation, vendors are introducing hardware and firmware support for virtualization-based confidential computing on mainline server platforms. Several OpenInfra projects introduced support for confidential computing features and the work goes on, motivated by stark interest from the user community. For example, since version Train OpenStack supports launching virtual machines with memory protection. The Kata containers community has been actively working on integrating support for virtualization-based confidential computing since early 2021. Its focus is currently primarily on IBM Protected Execution Facility (IBM PEF) and AMD Secure Encrypted Virtualization (AMD SEV) and its subsequent versions. Another upcoming technology — Intel Trusted Domain Extensions (Intel TDX) — is also in the scope but lagging behind as the hardware is not available yet. We hope to see other upcoming confidential computing technologies — such as ARM Confidential Computing Architecture (ARM CCA) — also supported by Kata Containers once hardware with ARM CCA becomes available. While the range of supported confidential computing features is already extensive, the Kata backlog is full of exciting issues to work on.
As it often comes with paradigm-changing technologies, implementing support for confidential computing is a bumpy ride: the technology stack supporting confidential computing is eclectic; moreover threat models implementation and functionality vary across vendor platforms and results in diverging capabilities, trade-offs and security guarantees. This is actually a good thing — since it allows addressing a more diverse set of use cases. However, to make the right choices that enable new security features without compromising functionality, it is also important to understand what are the capabilities and limitations of each confidential computing technology. The table below illustrates an overview of several aspects across four leading enterprise server architectures for confidential computing.
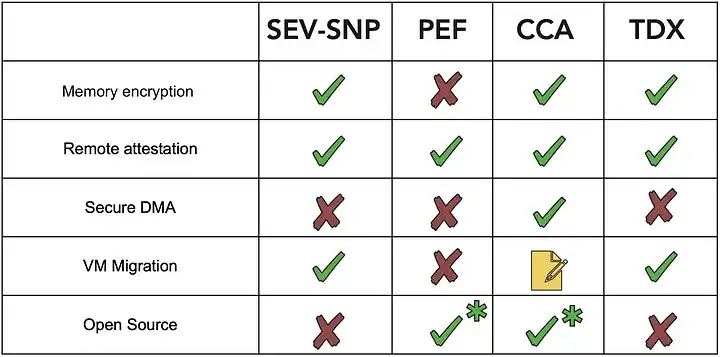
- Memory encryption is supported on most architectures, except for IBM PEF which opted for memory isolation (at least in OpenPOWER 9).
- Remote attestation is a defining feature of confidential computing. It helps to establish trust between the end user and the execution environment, by allowing end users to obtain a verifiable claim about the security properties of the trusted execution environment. Imagine the padlock in a web browser showing that an HTTPS connection is protected — except that this time it’s for workloads running in the cloud.
- Secure Direct Memory Access to confidential computing environments is tricky. So far, only ARM CCA features support for this in its specifications.
- Migration of Confidential Computing VMs has patchy support across the board; it is supported by AMD SEV-SNP and Intel TDX (in its specifications), is undefined for ARM CCA and is not supported out of the box in IBM PEF (at least according to a recent academic paper).
- Finally, open implementation helps both wider community adoption and building trust in the solution. Out of the four leading enterprise server architectures, only the IBM PEF ultravisor is available open source, while the ARM CCA specification is available to the licenses. The implementations of either AMD SEV-SNP or Intel TDX are not openly available at this point.
Knowing in depth the capabilities, trade-offs and limitations of confidential computing technologies is crucial to making full use of the functionality of each platform — whether it is Intel SGX, AMD SEV-SNP, IBM PEF, or the upcoming Intel TDX and ARM CCA. Thoughtful selection of the confidential computing technology can help address customer requirements with the best security guarantees and broadest functionality. CanaryBit uses this expertise to build its Confidential Cloud platform for secure data sharing. Confidential Cloud currently supports Intel SGX and AMD SEV-SNP and we are working on adding IBM PEF, Intel TDX and ARM CCA functionality whenever hardware support becomes broadly available. In a follow-up blog post we will review several use cases that can be addressed using confidential computing support in OpenStack and Kata containers. We already address some of them at CanaryBit through our confidential data collaboration SaaS.